To find the page that receives the attack, since we have a dedicated server and we have root access, we process the file on the server
|
1 |
/etc/httpd/conf/extra/httpd-info.conf |
and change the code as follows
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
... # Allow server status reports generated by mod_status, # with the URL of http://servername/server-status # Change the ".example.com" to match your domain to enable. <Location /a_difficult_name> SetHandler server-status </Location> # # ExtendedStatus controls whether Apache will generate "full" status # information (ExtendedStatus On) or just basic information (ExtendedStatus # Off) when the "server-status" handler is called. The default is Off. # ExtendedStatus On ... |
In the phrase “a_difficult_name” we write a name so that we can access it from a browser.
We restart the http server.
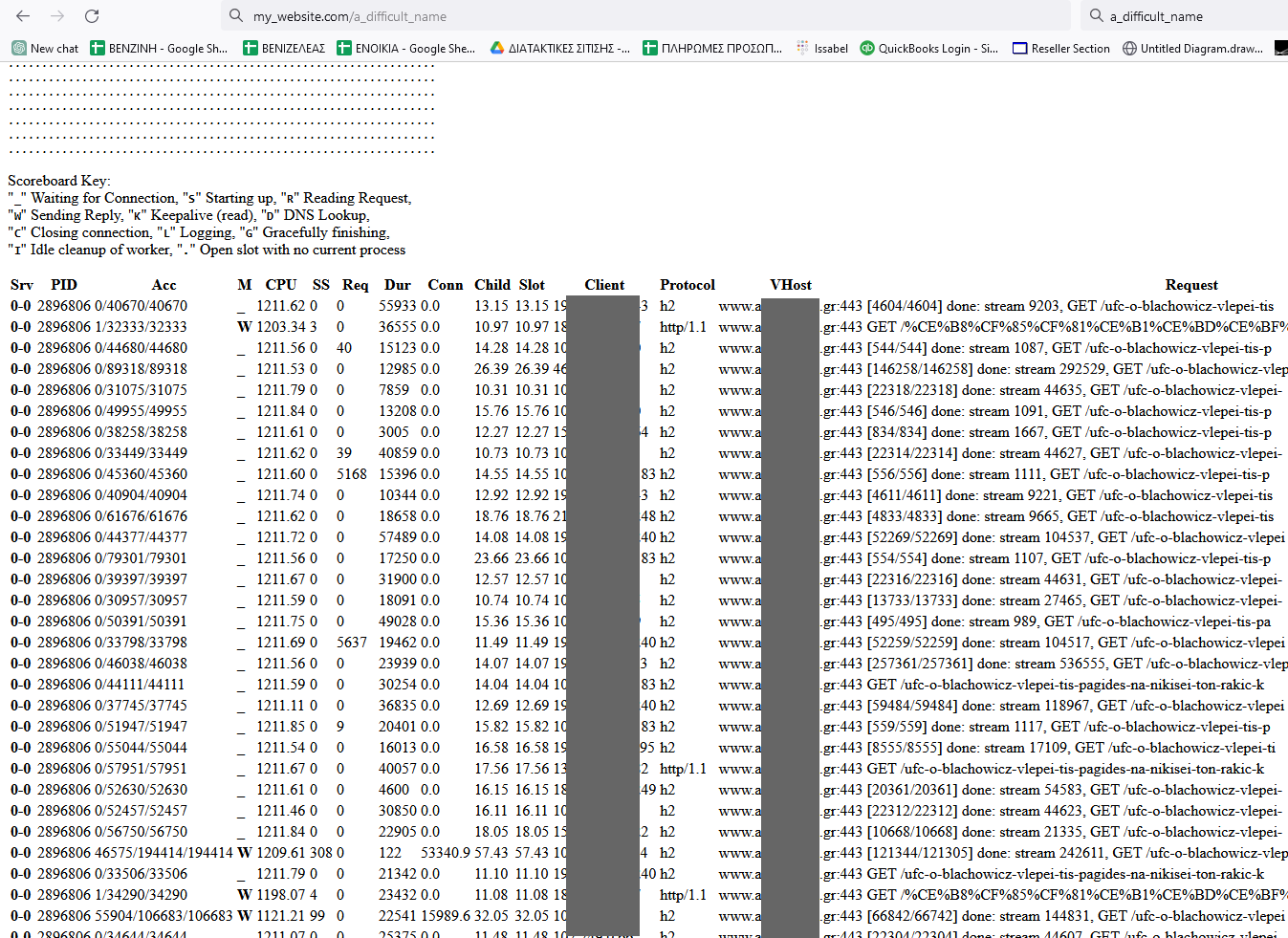
We write in the browser http://my_website.com/a_difficult_name
In this case we see that the page http://my_website.com/ufc-o-blachowicz-vlepei-tis-pagides-na-nikisei-ton-rakic-kai-pisteyei-oti-einai-o-epomenos-sti-seira is called quite often.
To block it, we divert it to some invalid website (eg http://fdjdfjkrftjtrjkwjktrjwst.com) by filling in the htaccess file.
|
1 |
Redirect 301 /ufc-o-blachowicz-vlepei-tis-pagides-na-nikisei-ton-rakic-kai-pisteyei-oti-einai-o-epomenos-sti-seira http://fdjdfjkrftjtrjkwjktrjwst.com |